Efficient video integrity analysis through container characterization
Abstract
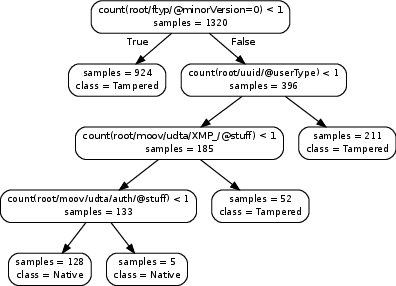
Most video forensic techniques look for traces within the data stream that are, however, mostly ineffective when dealing with strongly compressed or low resolution videos. Recent research highlighted that useful forensic traces are also left in the video container structure, thus offering the opportunity to understand the life-cycle of a video file without looking at the media stream itself. In this paper we introduce a container-based method to identify the software used to perform a video manipulation and, in most cases, the operating system of the source device. As opposed to the state of the art, the proposed method is both efficient and effective and can also provide a simple explanation for its decisions. This is achieved by using a decision-tree-based classifier applied to a vectorial representation of the video container structure. We conducted an extensive validation on a dataset of 7000 video files including both software manipulated contents (Ffmpeg, Exiftool, Adobe Premiere, Avidemux, and Kdenlive), and videos exchanged through social media platforms (Facebook, TikTok, Weibo and YouTube). This dataset has been made available to the research community. The proposed method achieves an accuracy of 97.6% in distinguishing pristine from tampered videos and classifying the editing software, even when the video is cut without re-encoding or when it is downscaled to the size of a thumbnail. Furthermore, it is capable of correctly identifying the operating system of the source device for most of the tampered videos.
BibTeX
@ARTICLE{yang2020efficient,
author={Yang, Pengpeng and Baracchi, Daniele and Iuliani, Massimo and Shullani, Dasara and Ni, Rongrong and Zhao, Yao and Piva, Alessandro},
journal={IEEE Journal of Selected Topics in Signal Processing},
title={Efficient Video Integrity Analysis Through Container Characterization},
year={2020},
volume={14},
number={5},
pages={947-954},
doi={10.1109/JSTSP.2020.3008088}
}
Acknowledgments
This work was supported in part by the National Key Research and Development of China (No. 2016YFB0800404), the National NSF of China (Nos. 61672090, 61532005, U1936212) and the Fundamental Research Funds for the Central Universities (Nos. 2018JBZ001, 2017YJS054). It was also supported in part by the Air Force Research Laboratory and in part by the Defense Advanced Research Projects Agency under Grant FA8750-16-2-0188. Finally it was supported by the Italian Ministry of Education, Universities and Research MIUR under Grant 2017Z595XS.